AWS Control Tower







AWS CT Landing Zone

This is set up when you 1st deploy the control tower in your environment.

Management account: central Hub for managing CT and managing an organization. CT is providing and configuring existing services work together and follow best practices.
AWS Organizations: That's the service CT is using to set up automation for the backbone of organizational structure within AWS.
sometimes you won't need to deploy security standards. That's the greater way to divide up Organizational Units (OUs). ex: we have super secure applications and will put them in their own ou. So we can apply a certain set of security best practices for those particular workloads.
Sandbox ou: give developers to try out services and features, run these experiments (limited amount of connectivity and a limited amount of damage )
Security ou: This includes an Audit account. That is a read-only account that gives access to CT login and views the information to complete the audit.
Log Archive Account: That is the centralized AWS cloud trail and config logs that going to include changes to all of the AWS resources done in your entire AWS account. One centralized place for auditing logs in your entire environment.
AWS Single Sign-On: SSO gives the ability to sign for another source or identity, by default SSO directory. But you can configure an external identity provider. once you sign with that external source then sso is give you permission across the entire environment. ( I have access to my sandbox and access to dev 1, dev 2, and pro account 1. You singing to sso you see a landing screen you choose all of the accounts you have access to and you can sign in to those individual accounts on the AWS console.)
That sso is setup in preconfigured by the control tower
AWS CloudFormation StackSets: this is a control tower that is used to change to an entire multi-account environment.
AWS Service Catalog: CT is used for Account Factory. everyone within the environment that has access to can go to that account factory and create any account in aws organization guidance and best practices.
CT Landing zone is also supports life cycle events. That means you can configure customer automation as part of new account creation. Always you can extend the functionality of the landing zone as you grow.
Initial Dashboard for control tower:

Preventive Guardrails: Block particular actions
Detective Gurdrails: Allow you to particular resources out of compliance over time
NonCompliant Resources: Any particular resources are across your current environment currently that might be violated one of your detective guardrail
You can see this dashboard all the environment and monitor on particular dashboards in our entire state.
Centralized Identity and Access, Logging & Monitoring



This is a dedicated account set up that automatically binds in the landing zone. There is a s3 bucket, that is managed by the account. every account in CT for it deployed is going to be configured to send a copy of cloud trail config logs to this log archive account

In some sort of emergency situation need access to manage the account, then you can use one of the cross-account roles in the security account to provide access to compromise the account.
This account recommends restrictions for the authorized account and personalizes comprehensive only. Only install security or audit tools into this account.
Automate Compliant Account Provisioning

Account factroy is a one of the core self service feature in CT enviremnt. Idea is here in that you can have service catalog . If you not have service catalog, service catalog create , manage and ditribute portpolio of the products to end users. Who then have access to product they need in the personalized portal.
ex: web server, DB server ; you can define configurations as a server as a product and have that entry in service catalog. Any one who has access to with in you entire envirement can go in to “hey I need to depoy database. Im going to deploy our one of the standerd database products that has been pre approved and pre valid set by the admins use the aws envirement”. You can controll the users to that have access to each product.

IN a CT landing zone the landing zone its selft use service catalog for the account factory.

Architecture overview of customization of control tower

CT Account Factory for Terraform

Establish Guardrails

Guardtails are control tower feature that audit your entire aws envirements for perticuler guardrails. Two different type of guardrails.
- Preventive
- Detective

In CT dashboard you can see which perticuler duardrails you want to apply to OUs, or endividual accounts. If you have a perticuler OU, has it own complience or regulatary requments you can apply different setup guardrails that OU and suppose to other OUs and that might be applice be under set up of govenence.
When we talk about guardrails, these are automations of the existing aws services.
Preventive: most of the guardrails are implement in CSPs. When you deploy and CSP whe to your OU that going to actually block oparations are happenning. we have SCP for users can only deploy for oncly ec2s that are T or N series. Someone goes to deploy C series that operation will be block by CSP.
Detective: These guardrails are once enforce with AWS config rules . EX: you dont have ssh access to SG. If you choose to enable and guardrails. Thats an optional. If you enble guardrail for perticular OU or Account then it going to be shutdown an instance that might be vialoting . But it give you notification on your CT dashboard , this perticulaer resourse in this perticuler account is out of complience with this guardrail. Detective guardrails are detect policy vialations and provide you and alert in the dashboard.
3 trypes of Guardtrails:
- mandatory
- recommended
- elective
Guardrail while in guidance
It also functions in regions where the AWS Control Tower is present, and as a result, the AWS Control Tower offers three distinct types of guidance: mandatory, strongly recommended, and elective guardrails.
- Mandatory
When a new landing zone is created, this category ensures that the guardrail is constantly enforced, and these restrictions are turned on automatically by default. They are affected by it. For example, untrusted users are unable to make any changes to the AWS infrastructure. Therefore, any regulations that fall under this must be labeled as “Mandatory.”
- Strongly recommended
In this subcategory, simply a few of the best practices that are implemented can result in an organization that is well-architected, and there is also the potential for many accounts. For instance, according to the policies of the organization, no bucket should be required to be public by default, and editing access should not be granted to anybody and everyone for those buckets. These kinds of policies will be of assistance in the process of putting into practise the most effective safety procedures within the firm.
- Elective guardrails:
Within an Amazon Web Services (AWS) enterprise environment, you may use elective guardrails to lock down or trace attempts to conduct commonly forbidden actions. These barriers are not activated by default and have the ability to be turned off.
Guardrails we can apply Account level or OU level.
The organization has the ability to choose the mode of the guardrails based on the requirements that they have. If the user gives it the instruction to operate in detection mode, then it will only recognise potentially harmful configurations of AWS resources. For example, if a company decides to implement a policy that states, “None of the S3 buckets that have been deployed should be accessible publicly,” Guardrail will recognise this violation of the policy and send a notification to all of the user’s registered email addresses informing them that the particular bucket in question has been made public by the offending user. Therefore, with the notification team’s help, they will be able to take the necessary precautions or activities to protect themselves. If Guardrails is set to operate in the preventative mode, then no user will be able to deploy a bucket that has public access enabled. This is because Guardrails will begin preventing the appropriate action and will protect the organizations from something that is going to deploy publicly.
Guardrail while in behavior:
Monitoring, recognizing when policies have been violated, and preventing an organization from violating policies are all possible uses for this tool.


Introduction to Multi Account Strategy in AWS Control Tower


whats the multi account envirement for keep these workloads isolated as simple billing structure, simple permission structure redusing some of the risk.
CT is setup aws organization units. This is the envirement we are working with below.




This is how to organiz that one account and break that up multi accounts envirement thats going to give you some benifits is billing , cleariy, isolation and permissions isolation.
It is possible to use AWS Control Tower If you alredy have existing AWS organization?


Migrate your existing aws organization structure if you one in the CT you want to complete with pre requisites
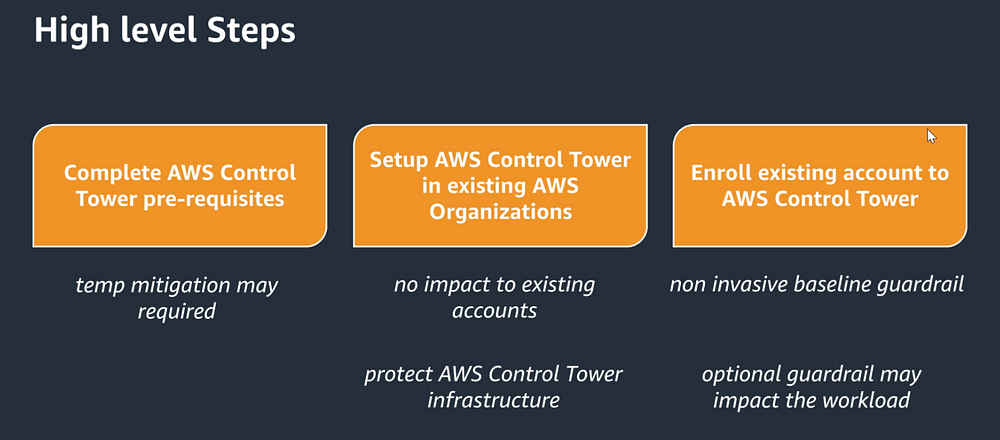
AWS Control Tower Extensions and Enhancements

more that just the applince comes with the house actually work how enhancements and extentions to CT. So we have 5 key usecases . Securty , Network management , identity management ,operation managemnet and globle security and compliance.
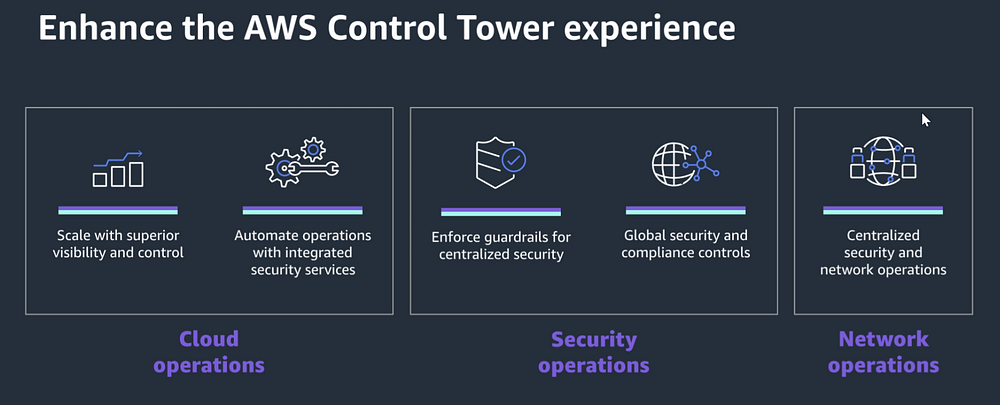
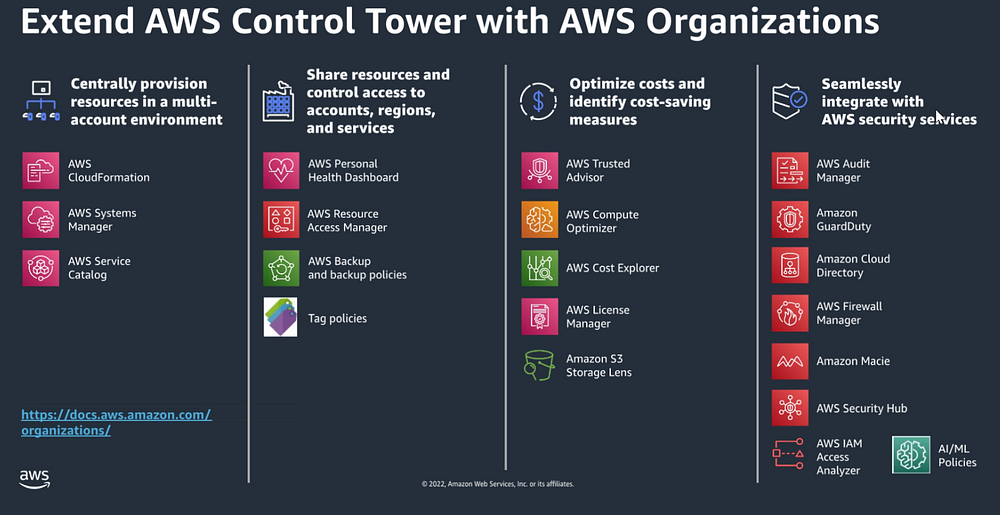



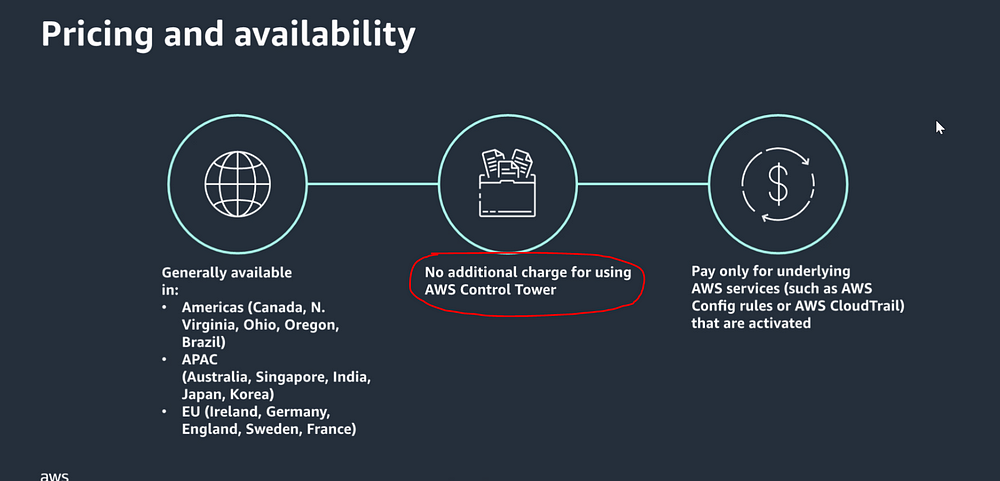
How to deploy Control Tower?


During the control Tower setup Landing zone is created automatically.
When some questions have. Whre is the region set up on your landing zone. When we create a control tower its create 2 mandadory OUs. its not a choice.
OU1: Securty (ou)— Log Archive and Audit accounts
OU2:Sandbox (ou)-optional OU— Sandbox account
Any other OUs that you build, no any other plicies are apply. You can customiz and enbale those policies.
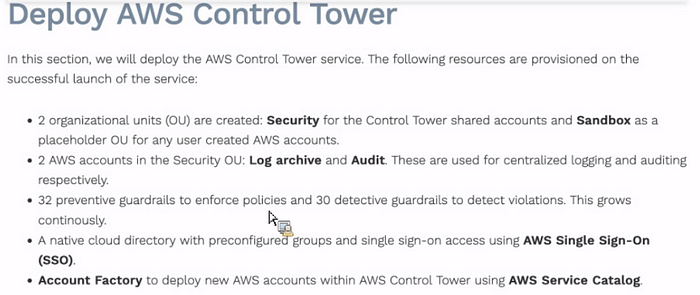
When you deploy the control tower you get fedarated single sign on access. You can use AWS SSO, now we can call “AWS Identity Center”. Adenticy center is provide derectory, but you want to provide external directoy like octa, microsoft active directry you can actually intergrate that as well. Account factory you can basically use provisioned accounts.
You want to deploy in a controll tower Managemnt Account.




In here we need to create 2 accounts. 1 account is specifically for log archive. These e mail has been unique.

In audit account enter new email address. this is 2 unique accounts. we want to 2 unique email address for create this 2 accounts.

CloudTrail is basically AWS organizational level. That gets enable.
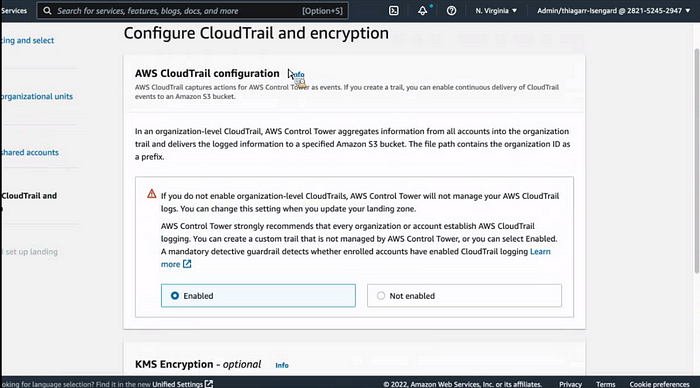
If you want to enable encryption , you can actually do that too. (this demo we are leave it)

Setup Landing Zone. This process take 60–90 mins complete.

Once the deployment is complete, you will see the organizational structure


This guardrails are basically on our foundational mandotory OUs.
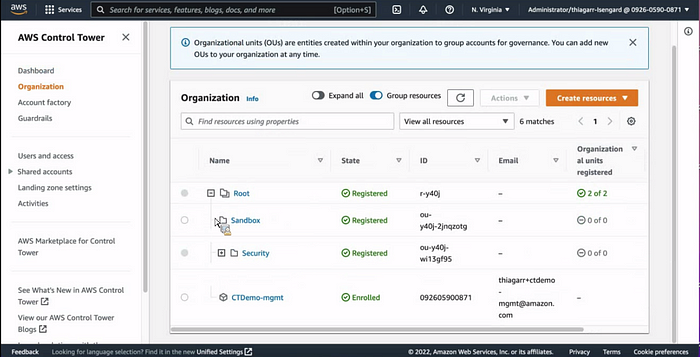
Sanbox and Securty Ous are in under the Root OU. You can creates multi levels of organizational structure. We can create up to 5 nested OUs. But it not be the right practice. Keep you organizational structure as simple.
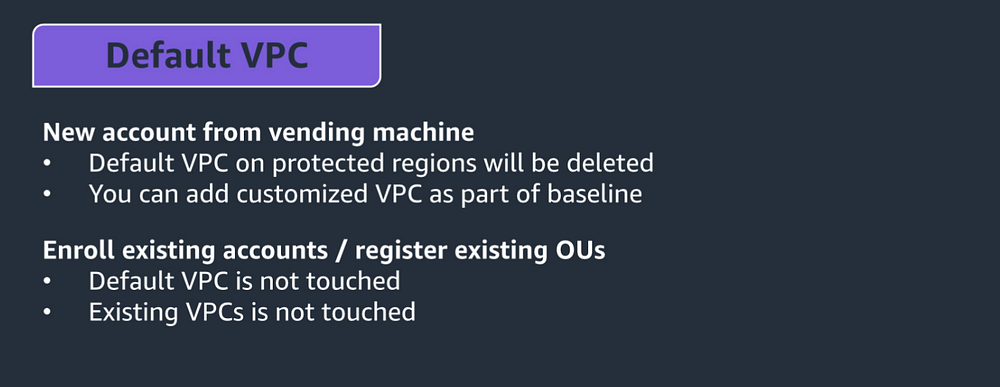
In Account factory you can create your accounts. When you create a AWS account via account factory default VPC is created this address range(172.31.0.0/16). But we can edit this vpc range.

If you select a region its will enabled(default vpc is created). Thats mean its will default at default vpc. but you dont select any region, that means its desabled.

Account Factory:

When you have create new account, you must have unique email address.

This process is take few minitues.
Create OUs:


You can like move the accounts between OUs too.
Add guardrails in OU:

How when deploy CT you get a landing zone. As part of the landing zone you will get sso.

AWS SSo provide directry and you can enable for users.

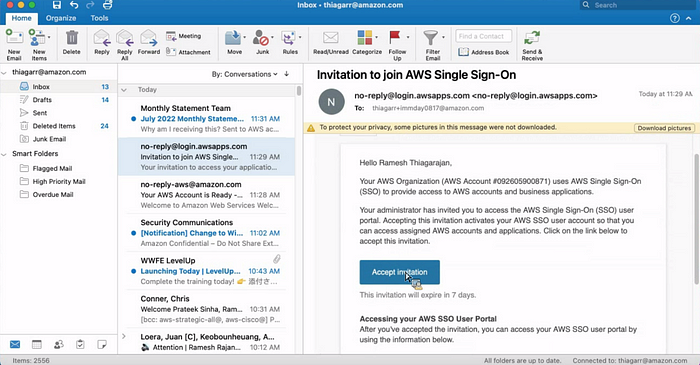




In member account:

you cant enble control tower in member account

Now we use a AWS provide SSO directry. We can use external directry.
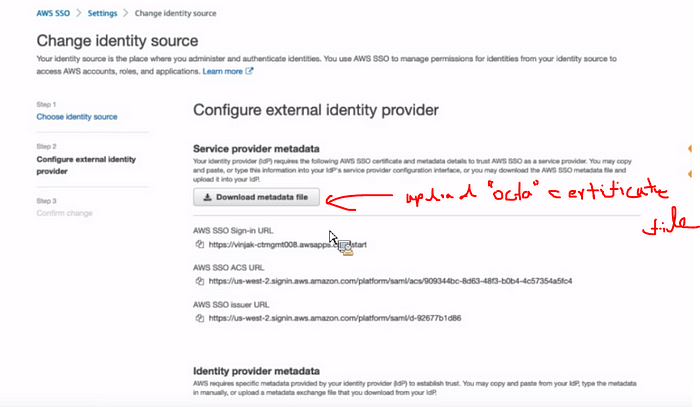
Then eny identy you will create in Octa, is availble in AWS identity center.

##############################################################
1) . Multi Account Strategy in AWS Control Tower

Benifits of using multiple AWS accounts:

Why suing multiple AWS accounts:

Muti account comes with more challanges. That why AWS organization comes in. AWS organization is Account management service. That enable you to consolidate multiple AWS accounts in to one singale organization.





Design principles for multiple AWS accounts:



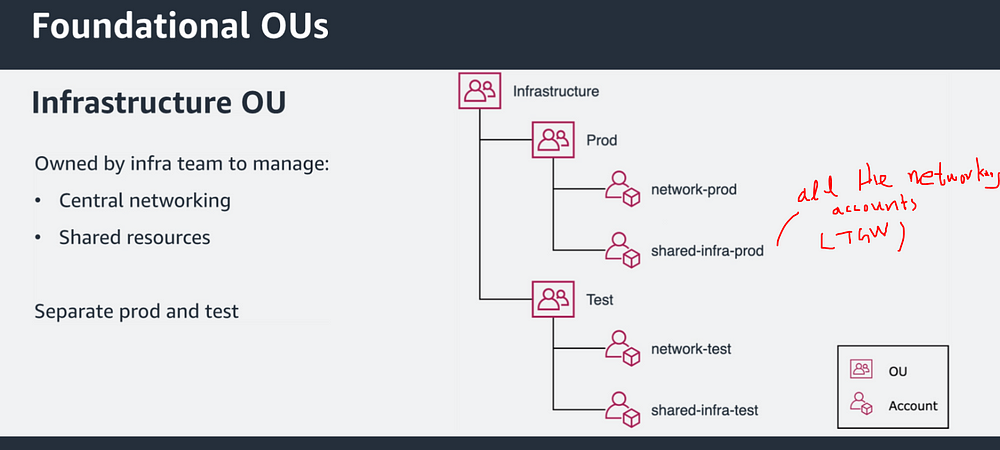
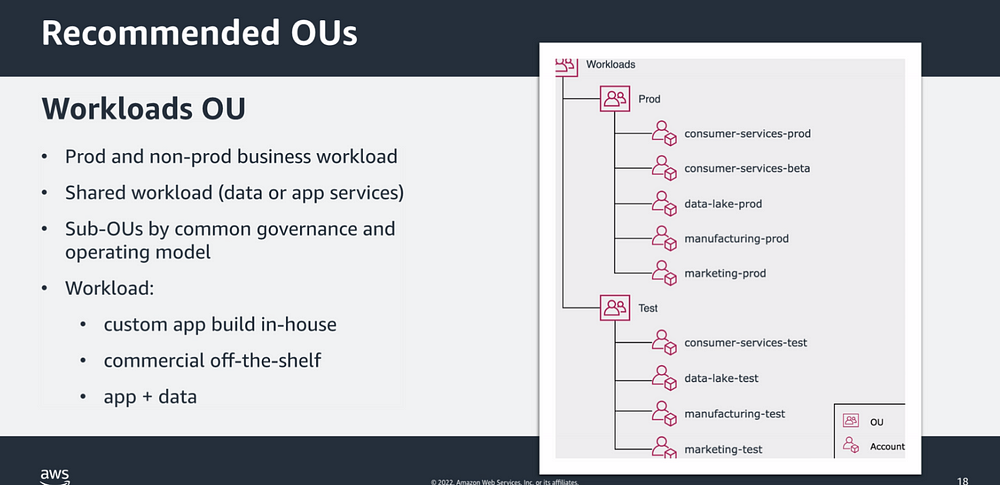
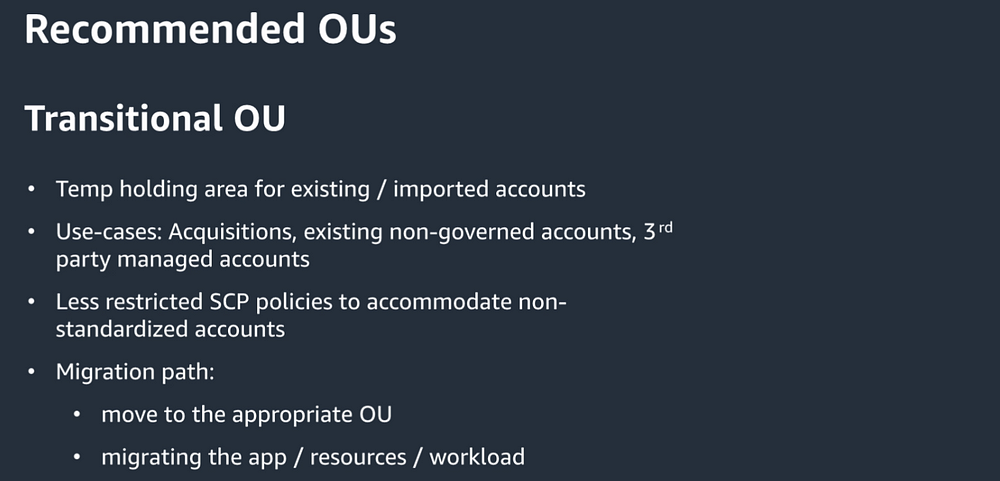
Recommended OUs:




2. Existing AWS Organizations




What happend during the setup?







Existing Account Entrollment:

we seen setting up controll tower in existing AWS organization. Now existing account entrollment. I have existing aws account and then I have setup my controll tower. Once I complete controll tower I might have entroll my existing accounts in control tower.

That aws account must be in the same ognization. then what we do is account wchich you are trying to envolve you will create a policy. Policy name is AWSContrilTowerExecution role. And then delete AWS config recorder and delivery channel.








DEMO:

create OU:



Now we can bring AWS account to OU. There are 2 ways for that.
- you have existing account, go to OU and enter account ID and its send the invitation to account admin. Once accept that invitation that account will be added.
- 2. Create accounr in Account Factory. refer below screenshots.


This process takes 5–10mins.

If you dont want the default VPC to be created ,


Logging to newly created AWS account via Administrator user permissions.